Peering in AWS allows you to connect 2 networks. The networks can be in different regions and even different accounts. As a result, resources that are on different networks can communicate with each other without any problems.
If you have several VPC networks in AWS and would like to combine them, peering is a great solution. Lambda functions, RDS bases or regular EC2s in different regions can communicate with each other in a secure way using private IP addresses. The best part is that it doesn’t require you to create any VPN gateways. Traffic takes place on AWS’s secure and fast backbone and does not need to leave it. Again, using peering, traffic stays on the internal AWS network and does not go over the internet.
Peering also gives us no single point of failure or bottleneck for bandwidth.
To connect 2 networks together via peering, you only need to configure 2 things:
- peering connection
- routing table
How to enable peering connection in AWS?
Enabling peering is really easy. Its configuration in the routing table does not cause many problems either. If you want to complicate your life, you can add additional rules in NACL and Security Group. However, I only recommend this if you want to limit web traffic and you really know what you are doing.
Peering connection
Just open the VPC, go to the Peering Connections tab in Virtual Private Cloud and click Create Peering Connection.
Now, all we have to do is give our connection a name and select the VPC networks we want to connect.
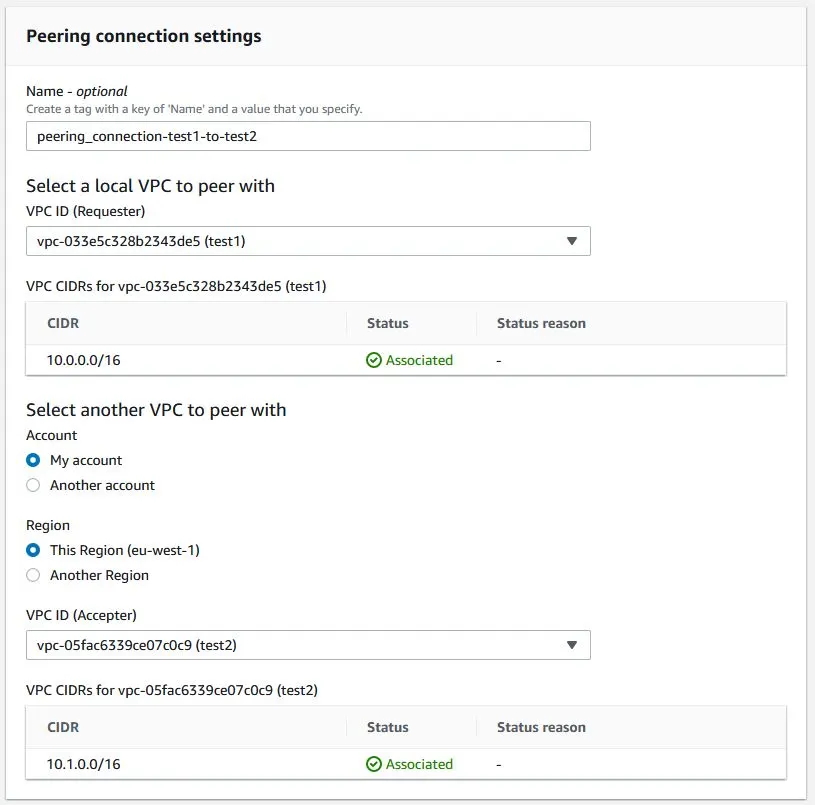
If you want to connect to the network on another account, just enter the ID of that account and the ID of the VCP network what you want to connect to, then log in to that account and accept the connection.
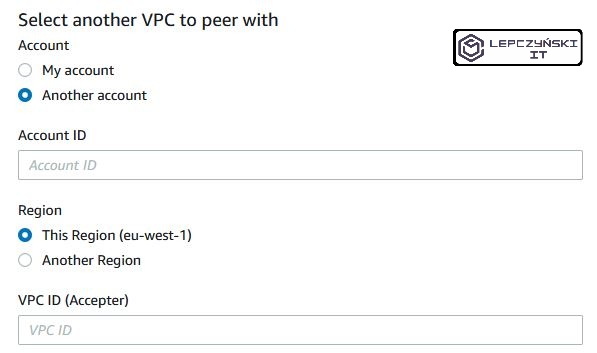
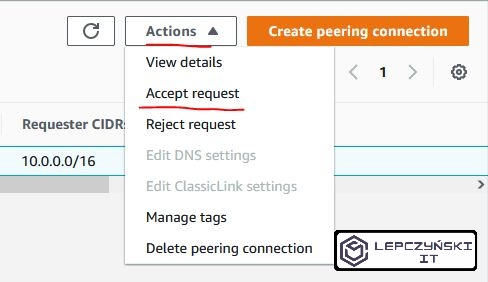
Exactly the same should be done if we combine networks under the same account. We need to select the peering connection that we have added, click “Actions” and “Accept request”.
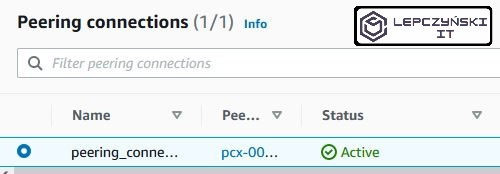
After we accept the connection, its Status should change to “Active“.
Routing table
Now both VPC networks are peering connected, but the EC2 machines that are in them yet cannot communicate with each other.
For correct communication of machines, an appropriate entry in the routing table should be added. To do this, select “Route Tables” from the menu on the left.
Then select the routing table that is assigned to the first network and from the “Actions” menu select “Edit routes“
Now the hardest part. Click on “Add route“. In the Destination field, enter the address of the second VPC network. In my case it is “10.1.0.0/16“. In the Target field, select Peering Connection and the name of this connection. Now you can click Save changes.
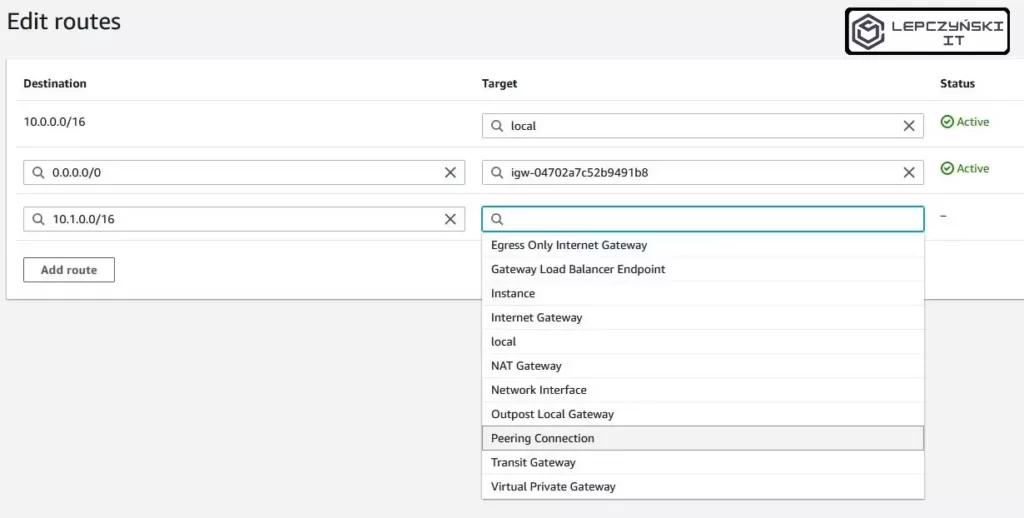
For the second web, do the same thing. Edit the routing table assigned to it and add a similar entry. This time only use the address of the first network in the Destination field, in my case it will be “10.0.0.0/16“. In the Target field, select Peering Connection and the name of this connection. Now you can click Save changes.
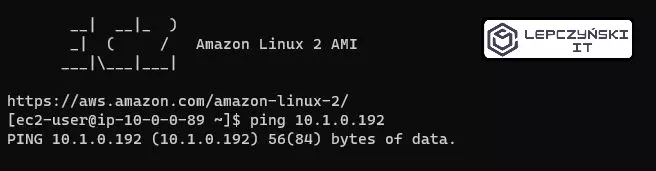
If you did everything right, the machines on both networks should be able to communicate with each other without any problem.
Now is the time to reduce the network’s ability to communicate with each other using NACL and Security Groups if you need to. Remember, always check that the connection is working at the beginning, and then configure the NACL and Security Group.
Peering connection problems
Note if you have just created a network, the routing table should be assigned to the network and subnets you want to connect to, and by default it is not. Go to your VPC routing table and check if it has subnets assigned.
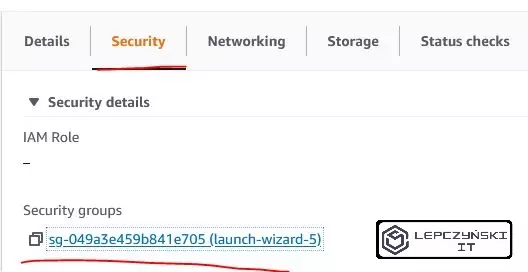
If you’ve done everything right but still can’t connect the EC2 machines to each other, then maybe the problem is with the Security Group. These groups, unlike NACL, have quite restrictive default settings (e.g. they prohibit pings). It’s worth taking a look at them. Check what groups you have assigned to EC2. Select the instance you are interested in, go to the Security tab and click Security groups.
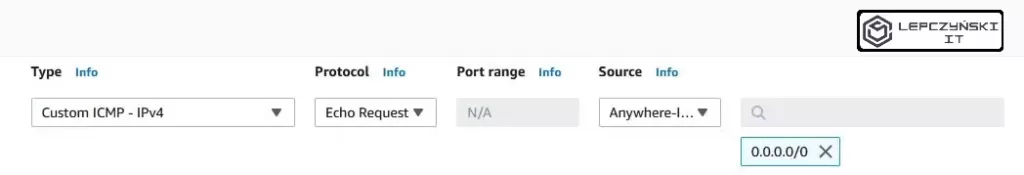
If you want to allow pings, open your Security Group and click Edit inbound rules. Then add the rule. Select the type Custom ICMP, protocol Echo Request and define the source. If you want to allow anyone to send queries from all addresses, then in source, select Anywhere and click Save rules. However, I urge you to narrow this scope down a bit. Although to the network from which you want to send such inquiries.
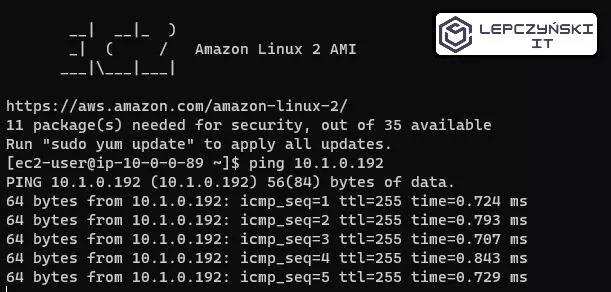
Now you should have no problem connecting and getting Echo Request.
Sample usage scenarios
Below you will find some sample peering scenarios.
Combination of 2 networks
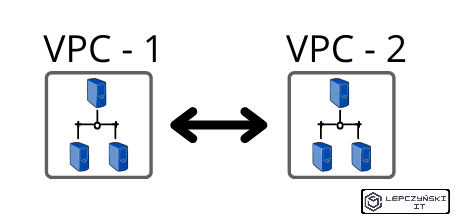
The simplest scenario where we only connect 2 networks together could be seen while reading this article and following the instructions in it step by step. Now I would like to highlight other common scenarios.
Combination of 3 networks
The peering connection is peer-to-peer, and there is no way to define it as transitive. It means that if we peering the network 1 with 2 and 2 with 3, we will be able to communicate only with networks with which we have established a connection directly.
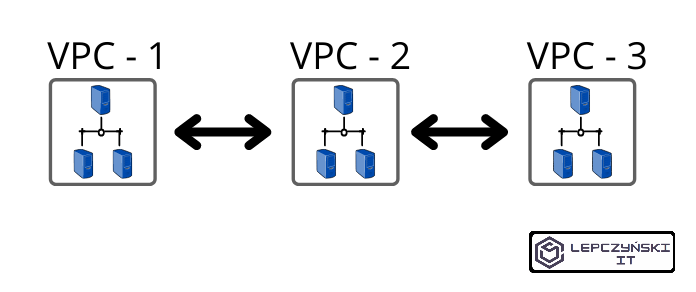
The network VPC-1 will be able to connect to VPC-2 but not to VPC-3.
The same applies to the network VPC-3, which will only be able to connect to the network VPC-2.
On the other hand, the network VPC-2 will be able to connect to both the VPC-1 and VPC-3 networks.
Thanks to this scenario, we maintain the isolation of the networks VPC-1 and VPC-3. We don’t allow them to communicate with each other, and at the same time we allow them to communicate with the VPC-2 network. To do this, we need to establish a second peernig connection. We do it exactly as described in the article, only this time, instead of connecting the VPC-1 and VPC-2 networks, we have to additionally connect the VPC-2 and VPC-3 networks. This means that we have to perform all the steps again for the new connection.
Connection to multiple networks
In this scenario, the hub network can connect to any network. The other networks can only connect to one main network located at the center.
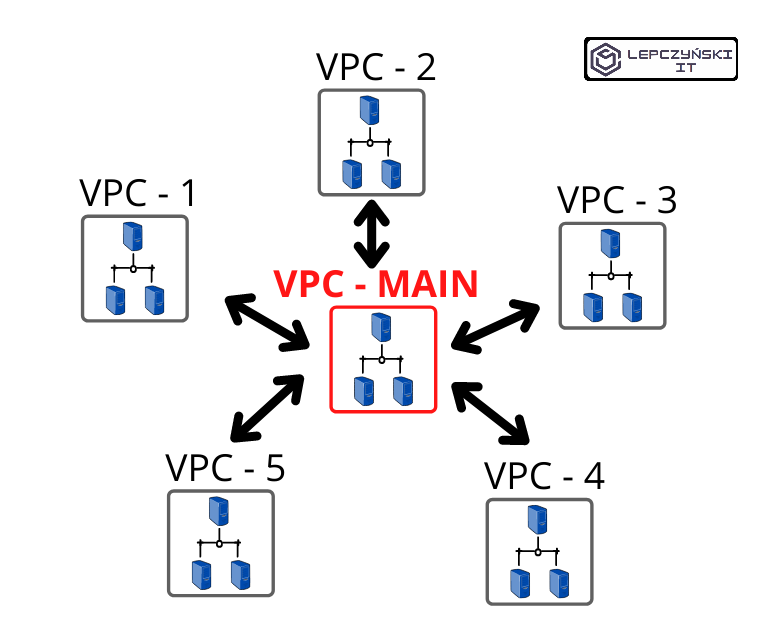
Here we repeat the steps needed to create a working peering connection as many times as the networks we want to connect to the network at the center of the VPC-MAIN.
It is a very common solution that may have for example, a monitoring server in the main network. The network VPC-MAIN is connected to any other network, so we can monitor everything without any problems. In such a central network, you will often find a file server, master document repository, or an image registry used for build, test, and deploy. We have one central place common to all networks. We have access to every network from it, and every network has access to it and nowhere else. Of course, it is good practice to limit some of this network traffic with NACL and Security Group.
Summary
The scenarios presented are a little idealized, because the web often looks like the one underneath, in a greatly simplified version. We have a lot of locations, even more networks, and clouds from several vendors, which does not make it any easier.
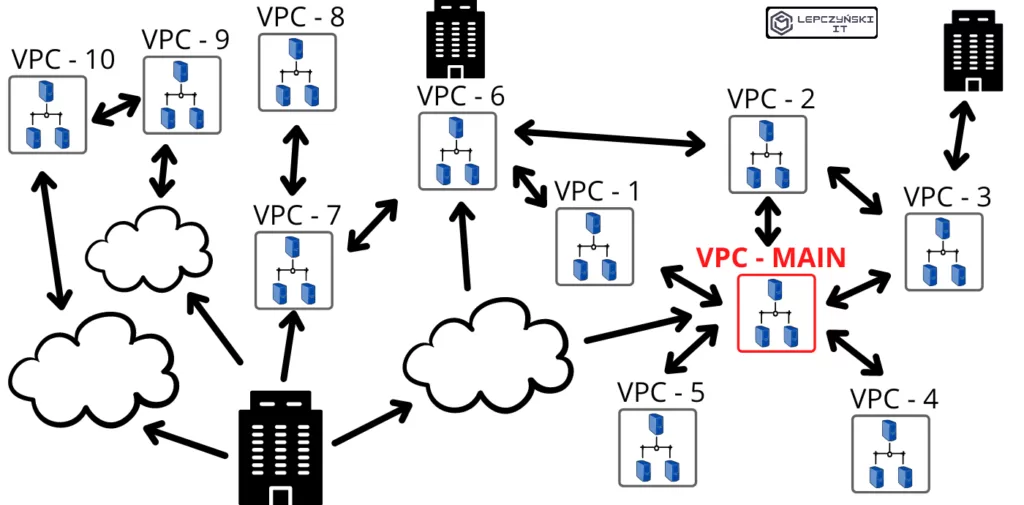
Anyway, it’s worth knowing what peering is and how you can use it, because it’s often useful.
Follow this link for AWS documentation about peering connection.
See the article ‘How to control costs in the AWS cloud‘. Enter the world of the cloud, increase your knowledge and increase your earnings.
