Some time ago I discovered that for added security and convenience you can use secrets from KeyVault in Azure function configuration. Sensitive data is more secure and less people can access it.
KeyVault
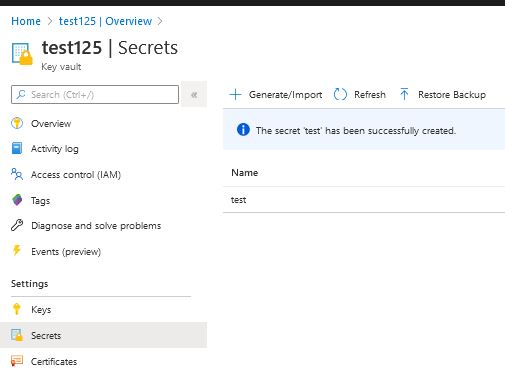
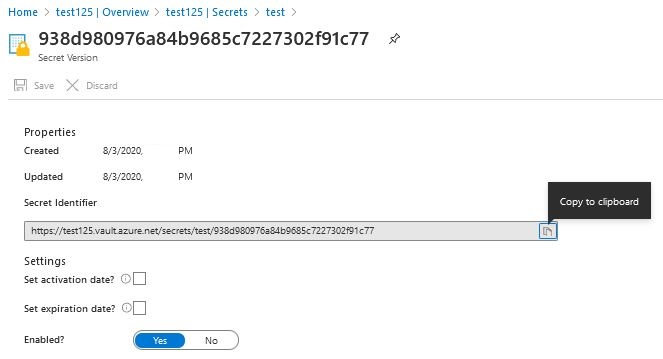
First, we create KeyVault and enter a secret into it. When we’re done, copy the ‘Secret Identifier‘ we’ll need later.
AppFunction
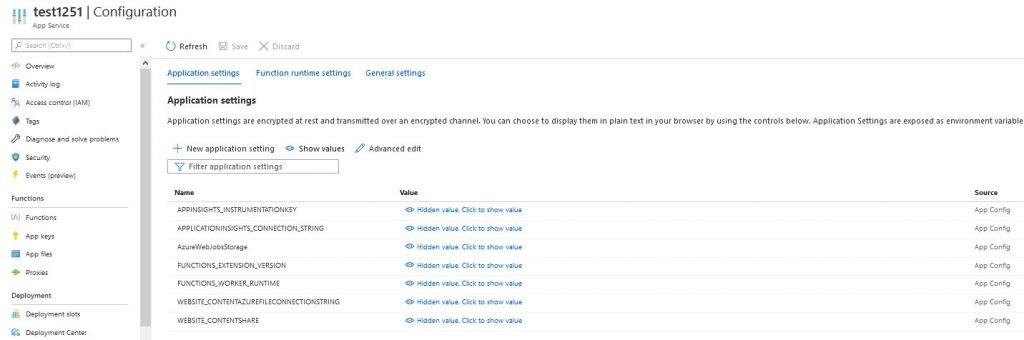
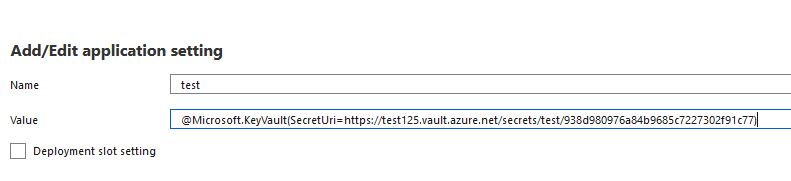
Now we can create AppFunction. For the app to be able to download secrets from KeyVault, click ‘Add / Edit application setting‘, enter any name and enter the value @Microsoft.KeyVault(SecretUri=<KeyVault_ Secret_Identifier>)
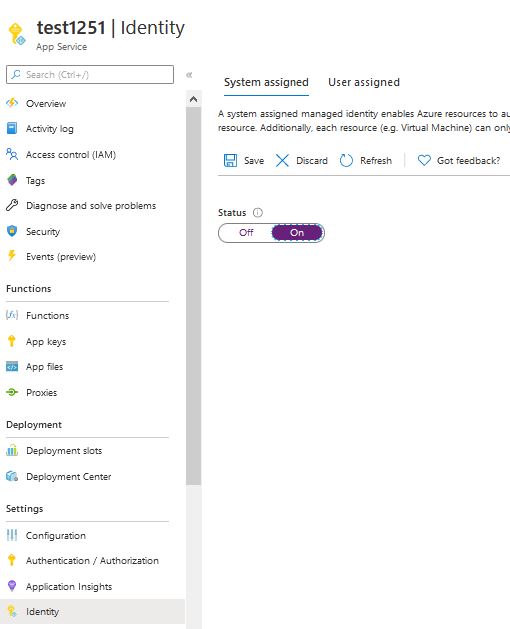
For Azure App Function to read the secret, you still need to create an identity for the function and grant it permissions in KeyVault. We create the identity by changing the status to ON and clicking save. We copy ‘Object ID‘ will be needed later.
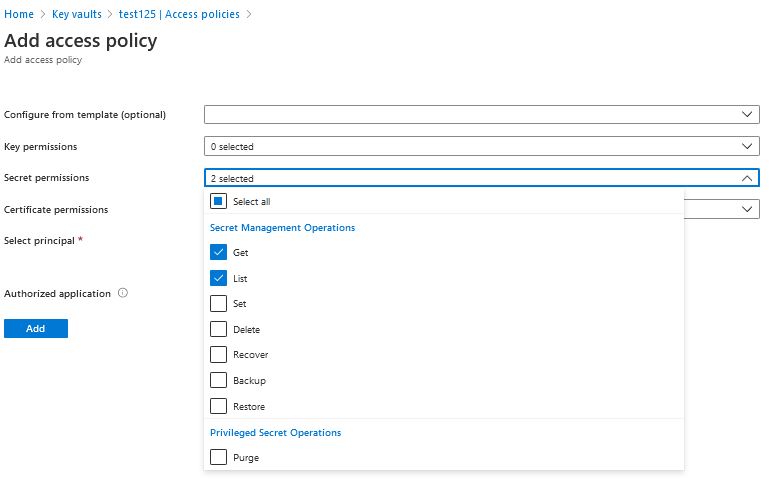
We open KeyVault and add a policy by clicking on ‘add Access Policy‘. We only give the necessary Get and List permissions for Secrets, in select principal we add ‘Object ID‘ to our Azure AppFunction.
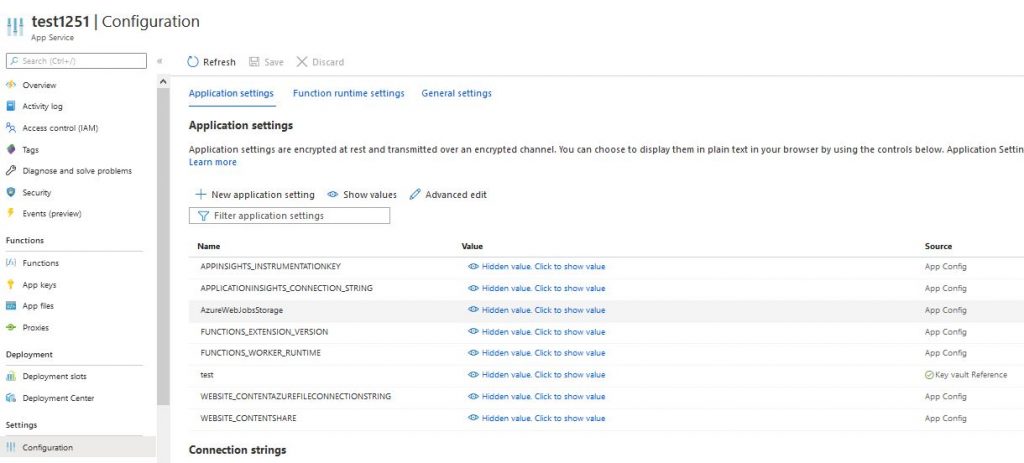
If we did everything right, then after clicking refresh in the configuration of our function, we should see the value of Key vault Reference with a green mark.
More information on Azure function can be found here https://docs.microsoft.com/pl-pl/azure/azure-functions/
More information on Key Vault can be found here https://docs.microsoft.com/pl-pl/azure/key-vault/
If you liked the article, see also my other posts https://lepczynski.it/en/azure_en/azure-keyvault-permanently-delete-a-secret/
