In this article you will learn how to get instance_ID ami_ID and other EC2 information from ec2. I’ll show you two ways to do it. I will tell you about the best practices and give you good advice. This is extremely helpful when you’re creating a script or getting started with automation. You will learn what are the differences between IMDS and IMDSv2.
IMDSv1
Sometimes, working on ec2 virtual machine, you’d like to quickly check the instance_ID or other parameters. This can be done in several ways. First, let me tell you about Instance Metadata Services, which is IMDS and the old way.
So on AWS, Instance Metadata Service (IMDS) allows you to access data about your ec2 instance which you can use to configure or manage a running instance.
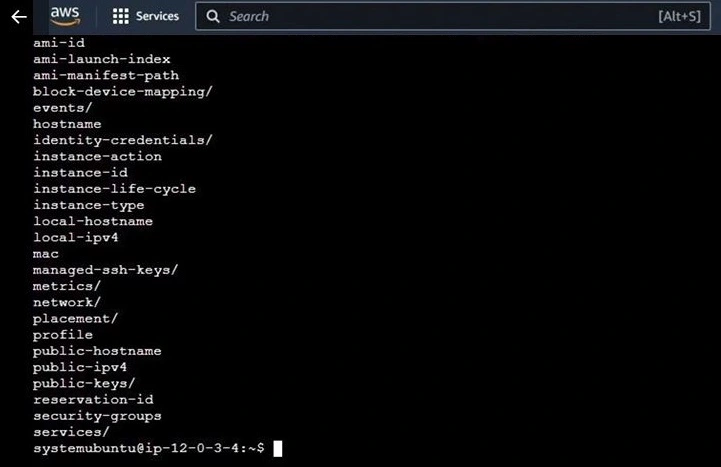
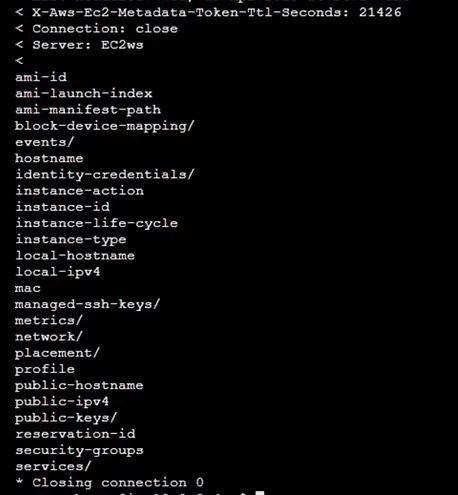
Instance metadata are available in many categories, for example, hostname, network, ami-id, etc. if you want to read the instance ID, you can use this command
curl http://169.254.169.254/latest/meta-data/instance-idor
wget -q -O - http://169.254.169.254/latest/meta-data/instance-idThe address 169.254.169.254 is a special IP address in AWS. By using it on ec2 you are referring to the machine you are currently logged in to. It’s an important address, so good advice from me, you’d better remember that IP address or write it down somewhere. This is especially useful for scripting and automation. Of course if you are using IPv6 you can use this fd00:ec2::254 http://[fd00:ec2::254]/latest/meta-data/.
To avoid constantly updating the script, it’s best to use latest (as in the examples above) rather than a version number.
IMDSv2
There is a better and safer way to read this information. It is a new IMDS called IMDSv2. IMDSv2 uses session-oriented requests. According to the documentation, each request is now protected by session authentication.
You can start a session with a simple HTTP PUT request to IMDSv2. After that IMDSv2 returns you a secret token and you can use the token as a password to make requests to IMDSv2 for metadata and credentials.
Important information about IMDSv2:
- There is no limit to the number of tokens.
- There is no limit to the number of sessions.
- The new version is still limited by normal IMDS connection and throttling limits.
- Sessions can last up to six hours, that is, up to 21600 seconds
- The session token can only be used directly from the EC2 instance where that session started.
Let’s go deeper, first generate a token with the following command:
TOKEN=`curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600"`As you can see, the request must contain a header specifying the time to live (TTL) for the token in seconds, as I have already written up to a maximum of six hours.
Then use the token, for example with the following command:
curl -H "X-aws-ec2-metadata-token: $TOKEN" -v http://169.254.169.254/latest/meta-data/You can get instance_id for example using this command:
TOKEN=curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" && curl -H "X-aws-ec2-metadata-token: $TOKEN" -v http://169.254.169.254/latest/meta-data/instance-id/You can get subnet information with:
TOKEN=curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" \
&& curl -H "X-aws-ec2-metadata-token: $TOKEN" -v http://169.254.169.254/latest/meta-data/network/interfaces/macsTOKEN=curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" \
&& curl -H "X-aws-ec2-metadata-token: $TOKEN" -v http://169.254.169.254/latest/meta-data/network/interfaces/macs/02:29:96:8f:6a:2d/subnet-id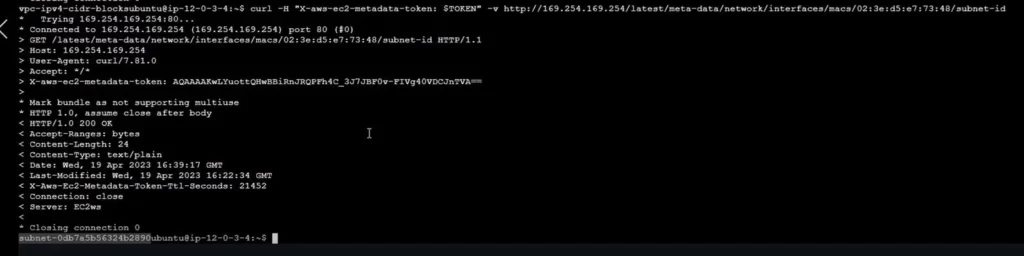
Of course, you can read much more information:
Instance Identity Document
I can also tell you that every ec2 instance that is started has an instance identity document which contains information about the instance itself.
You can use instance identity document to validate ec2 attributes. The instance identity document is provided in plain text JSON format via the Instance Metadata Service (IMDS). The instance identity document is generated when ec2 is stopped and started, or restarted.
wget -q -O - http://169.254.169.254/latest/dynamic/instance-identity/document
TOKEN=`curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600"` \
&& curl -H "X-aws-ec2-metadata-token: $TOKEN" -v http://169.254.169.254/latest/dynamic/instance-identity/document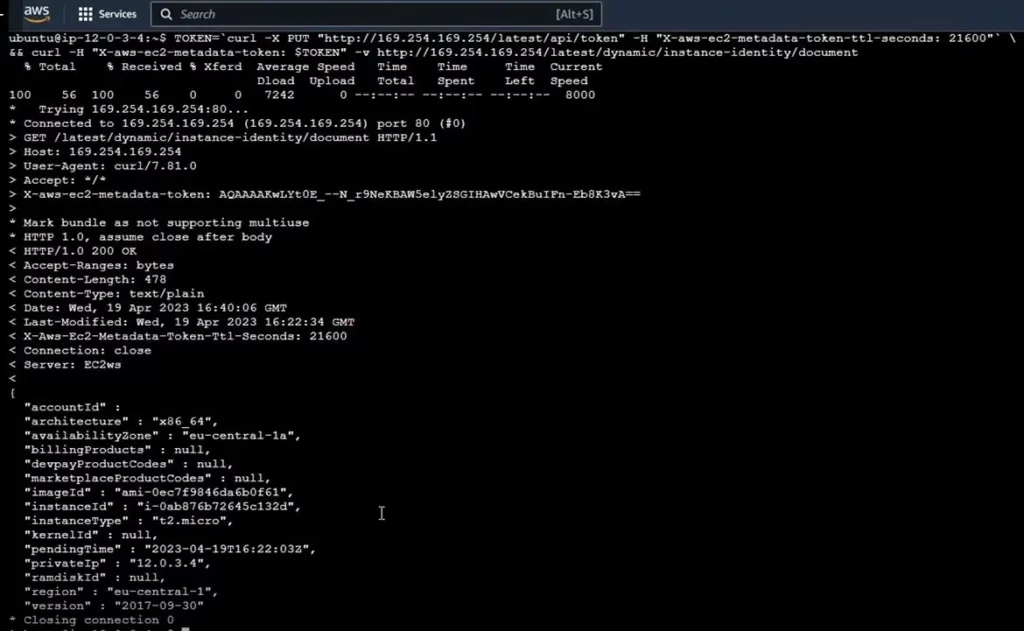
By the way, you can also find the instance_id stored in a file on your ec2 in the location /var/lib/cloud/data/instance-id.
clou-utils
Something extra. I don’t know if you know, but if you want to get information about your ec2, you can also install cloud-utils.
sudo apt-get install cloud-utilsThis allows you to easily read ec2 information such as instance_id as in the previous example:
ec2metadata --instance-idOf course you can read much more information, try using:
ec2metadata -h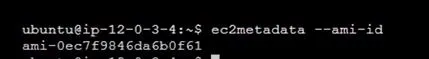
user data
User data is also very interesting. This is a set of commands that can be passed to an instance at startup. After starting ec2, the instance executes the commands contained in user data with root privileges.
Each instance has access to user data using, for example, the command:
curl http://169.254.169.254/latest/user-dataNiestety wiele osób podaje tam dane wrażliwe i czasami możemy znaleźć tutaj loginy i hasła. Proszę, Ty tego nie rób.
Unfortunately, many people provide sensitive data there and sometimes we can find logins and passwords here. Please don’t do something like that.
Summary
I hope you already know what is the difference between IMDS and IMDSv2 and why it is worth using IMDSv2. One last piece of advice, if you want, you can block the use of IMDSv1 and force the use of IMDSv2. You will learn how to do it in my video How to get information about ec2 from ec2 (IMDS) Best Practices & Practical demo tutorial 2023.